The security researcher Fabian Bräunlein from positive.security in Berlin shows once again with a replica AirTag that Apple’s “Find my” Network that you can be used to track things like AirTags is not as advanced in terms of security as you would like.
So far, Apple has had to take some criticism because AirTags can be muted very quickly and they are often used as stalking devices. Apple is always trying to prevent abuse with more information on the iPhone, but the problems seem to be much deeper.
Any devices can be registered in Apple’s tracking network
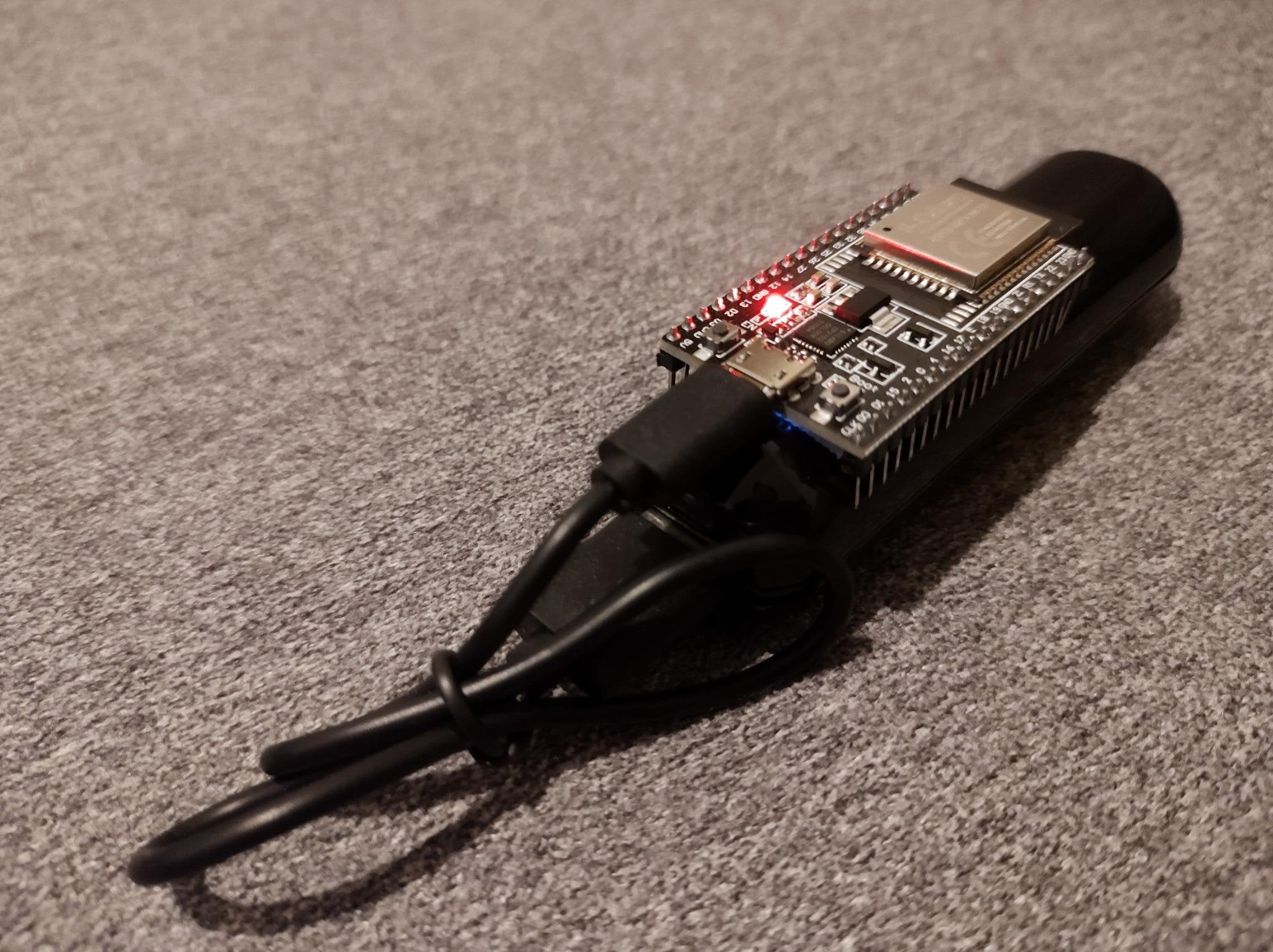
Some time ago, the security researchers at the Technical University of Darmstadt developed OpenHaystack, an option that allows you to use your own Bluetooth devices via Apple’s “Find my” tracking network. Fabian Bräunlein has now expanded this and combined a cheap ESP32 with a power bank and smart software. And lo and behold: the friend who was in to test it hasn’t found the device for five days. The reasons for this are surprising if you expect, as usual, that Apple would run a fairly closed system.
IDs of fake AirTags are also fake
So just about any Bluetooth device can use Apple’s “Find my” use network. Although the replica has no serial number at all, Apple allows it to be operated on the network. The necessary Apple ID for retrieving the geo-information can still be created anonymously – so here too is no verification of the user. Worst of all: the security researcher managed to install software on the ESP32 that simply randomly emits 2000 different IDs. As a result, Apple’s warning about alien AirTags doesn’t work – after all, the system always thinks there’s a new AirTag nearby, even though it’s the same one. Needless to say, the replica does not contain a speaker either, so as not to draw attention to itself.
positive.security points out that Apple should urgently pay attention to the infrastructure when considering security, and not just to the misuse of some users that is already taking place. For a company that operates a closed app store, sells iPhones that need to be activated and even links hardware components in iPhones to the serial number of the motherboard, it is almost absurd that this does not happen with tracking devices.
The “Find my” Network seems insecure and you provide it
Using the tracking network can be done with any device without a serial number, with an anonymous Apple ID and the warning function can be overridden with simple artificially generated IDs. We would actually have expected that every AirTag would be permanently connected to the Apple server via an ID that was fixed in the chip and could simply be deactivated in the event of misuse. But currently it is easy and ironically cheaper to build your own copy for the tracking network.
If you don’t like this surveillance story, you also have a moral problem: not using AirTags is not enough. If you use Apple devices, they will be used to track corresponding Bluetooth devices, whether you want them to or not. So you have no way of preventing this abuse. Apple does not allow you to opt out of using your Apple devices on this network. So, for better or for worse, you are part of this infrastructure.