Anyone who has a lot of smart home devices at home and perhaps also does home office work will probably have already done the work of separating the two areas. After all, you never know how the sometimes cheap hardware will behave in your own network. Two separate networks are very advantageous.
But even if you have already done this, hardware may have accumulated over the years that logs into the Smart Home WLAN and has been receiving security updates for a long time – or simply never. The biggest security hole in the WLAN area was KRACK for WPA2 encryption. With this method, some devices could be confused by attackers and the login key was sent out again – and intercepted by the attacker. Security updates for your routers and devices eliminated this.
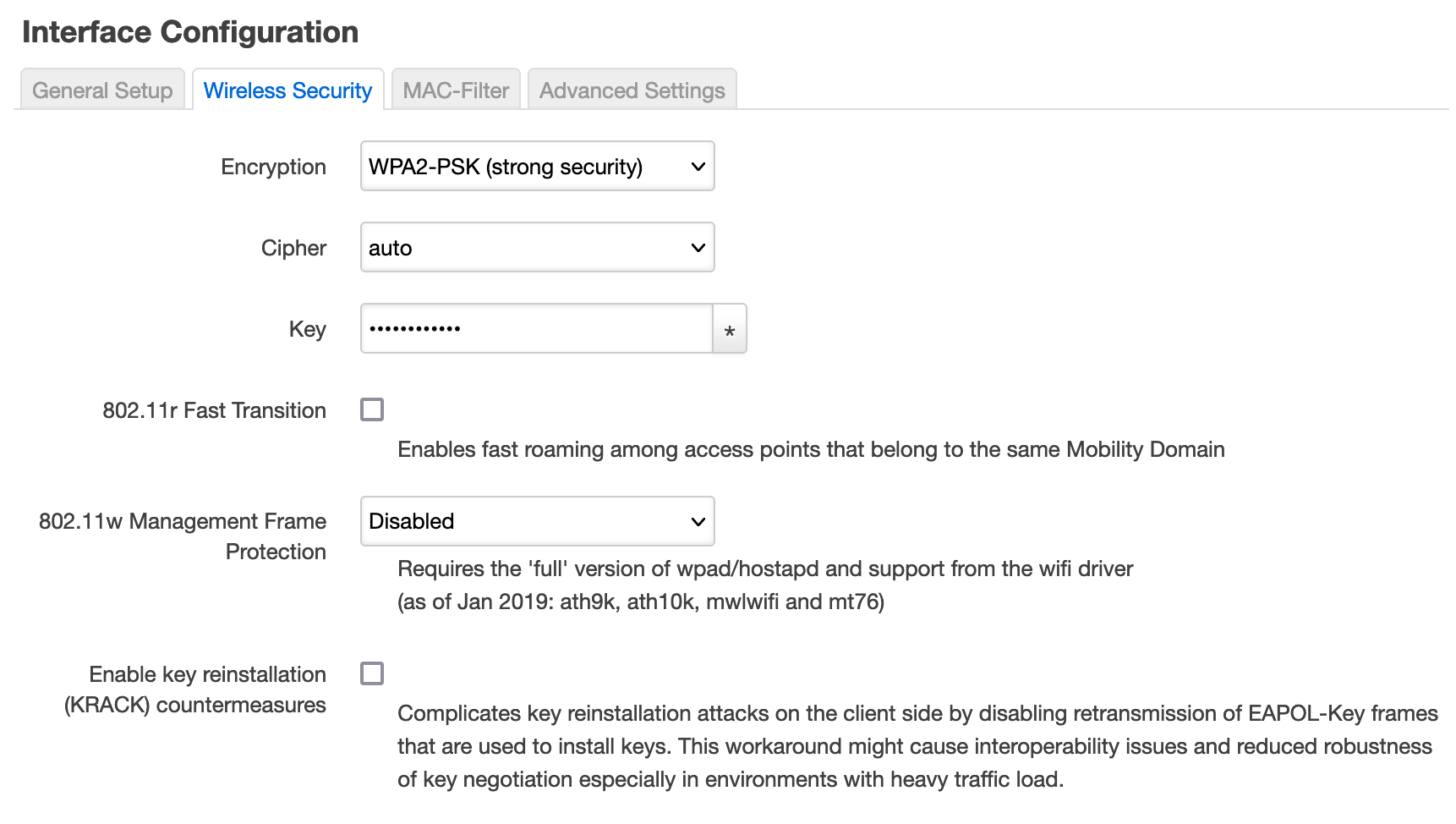
OpenWRT offers a security option for old WLAN hardware
But as said, there is old hardware that still falls for it. This can be solved if you use a router with OpenWRT: you can enable an option in the WLAN settings that prevents the connection key from being requested again. Very useful.
However, this can lead to problems when pairing devices for the first time, because sometimes the keys just don’t arrive and have to be sent again. In that case, you simply have to trigger the pairing process more. Or simply disable this option for the time of the first connection. This was the case with our Yeelight S1 (which of course does not count as old hardware), for example.
If the connection between the devices is established, you can enable the security function in OpenWRT again. Our Yeelight lamp then connected to the WLAN without any problems.